Secure IT Solutions – The Foundation of Modern Business Security
In today’s digital economy, businesses rely heavily on technology. From cloud platforms and email systems to payment processing and customer databases, nearly every operation depends on IT infrastructure. But as technology grows, so do cyber threats. This is where secure IT solutions become critical.
Secure IT solutions are comprehensive systems designed to protect networks, devices, data, and digital operations from cyberattacks, breaches, and unauthorized access. They are not just antivirus tools or firewalls. They are layered, strategic, and continuously monitored protection frameworks.
Cybercrime is increasing every year. Global reports estimate that cybercrime damages will reach trillions of dollars annually. Small businesses, mid-sized companies, and large enterprises are all targets. Attackers no longer focus only on large corporations. In fact, smaller organizations are often targeted because they lack strong security measures.http://bestbuygeeksquads.com
Without secure IT solutions, businesses face:
- Data breaches
- Financial loss
- Operational downtime
- Legal penalties
- Reputation damage
- Loss of customer trust
Modern secure IT solutions combine technology, policies, monitoring tools, and compliance strategies to create a protective shield around business operations.
Security is no longer optional. It is a business necessity.
Why Secure IT Solutions Matter More Than Ever
The way businesses operate has changed dramatically in the past decade. Remote work, cloud computing, mobile devices, and digital transformation have expanded the digital attack surface.
Here’s what has increased risk:
- Employees accessing systems from home networks
- Increased use of cloud storage
- Third-party software integrations
- Online payment processing
- IoT and smart devices
Each of these creates new entry points for cybercriminals.
Secure IT solutions address these risks by implementing:
- Network protection systems
- Endpoint security tools
- Cloud security frameworks
- Data encryption protocols
- Identity and access management systems
- 24/7 threat monitoring
Businesses that invest in secure IT infrastructure gain stability, resilience, and long-term protection.
The Cost of Ignoring Secure IT Solutions
Some business owners hesitate to invest in cybersecurity because they see it as an expense. However, ignoring secure IT solutions can be far more costly.
Financial Impact of a Data Breach
| Cost Category | Potential Impact |
|---|---|
| System Recovery | High |
| Legal Fees | High |
| Regulatory Fines | Severe |
| Customer Compensation | Moderate to High |
| Downtime Loss | Significant |
| Reputation Damage | Long-Term |
A single breach can cost hundreds of thousands or even millions of dollars depending on the business size.
In comparison, investing in secure IT solutions is predictable and manageable.
Prevention always costs less than recovery.
What You Will Learn in This Guide on Secure IT Solutions
This in-depth guide will cover:
- What secure IT solutions actually are
- The types of IT security systems businesses need
- Why secure IT infrastructure is critical today
- How to choose the right IT security provider
- Costs and pricing structures
- Latest trends in cybersecurity
- Step-by-step implementation strategies
- Common mistakes to avoid
By the end of this article, you will have a clear understanding of how secure IT solutions protect businesses and why every organization must prioritize IT security in 2026 and beyond.
What Are Secure IT Solutions?
To fully understand why businesses need secure IT solutions, we must first define what they truly mean.
Secure IT solutions refer to a comprehensive set of technologies, processes, and security strategies designed to protect an organization’s entire IT environment. This includes networks, devices, cloud platforms, databases, software systems, and user access points.
Unlike basic IT support, which focuses on fixing technical problems after they occur, secure IT solutions are proactive. They are built to prevent threats before damage happens.
In simple terms:
- IT support keeps systems running.
- Secure IT solutions keep systems protected.
Modern businesses cannot rely on single tools like antivirus software alone. Cyber threats today are complex, automated, and constantly evolving. That is why secure IT infrastructure requires a multi-layered security approach.
The Core Purpose of Secure IT Solutions
The primary goal of secure IT solutions is to reduce risk while maintaining operational efficiency.
They aim to:
- Prevent unauthorized access
- Detect suspicious activity in real time
- Protect sensitive business and customer data
- Ensure business continuity
- Maintain compliance with regulations
- Minimize downtime
Secure IT solutions work continuously in the background. Most of the time, if they are working correctly, you will not even notice them. Their purpose is silent protection.
Key Components of Secure IT Solutions
Effective secure IT solutions combine multiple security layers. Each layer protects a different part of the IT ecosystem.
1. Network Security
Network security protects data as it travels across systems.
It includes:
- Firewalls
- Intrusion detection systems
- Traffic monitoring
- Network segmentation
- Secure VPN connections
Network protection acts as the first line of defense. If the network is compromised, everything connected to it becomes vulnerable.
2. Endpoint Security
Endpoints include laptops, smartphones, desktops, and servers. Each connected device is a potential entry point for attackers.
Secure IT solutions protect endpoints through:
- Advanced antivirus software
- Endpoint Detection and Response (EDR)
- Automatic updates and patch management
- Device encryption
With remote work increasing, endpoint security has become a critical pillar of secure IT infrastructure.
3. Cloud Security
Most businesses now rely on cloud platforms for storage, collaboration, and operations.
Secure IT solutions ensure cloud safety through:
- Secure configuration management
- Encrypted data storage
- Multi-factor authentication
- Access control policies
- Continuous cloud monitoring
Cloud misconfigurations are one of the leading causes of modern data breaches. Proper cloud security prevents accidental exposure.
4. Data Protection and Encryption
Data is one of the most valuable business assets.
Secure IT solutions protect data using:
- Encryption at rest and in transit
- Secure backup systems
- Disaster recovery planning
- Data loss prevention tools
Even if attackers gain access to encrypted data, they cannot read it without authorization keys.
5. Identity and Access Management (IAM)
Not every employee needs access to every system.
Identity and access management ensures:
- Role-based access control
- Multi-factor authentication
- Secure login policies
- Monitoring of user behavior
Many cyberattacks begin with stolen credentials. IAM reduces this risk significantly.
6. Continuous Monitoring and Threat Detection
Modern secure IT solutions rely heavily on real-time monitoring.
Advanced systems use:
- Security Information and Event Management (SIEM)
- AI-powered threat detection
- Behavioral analysis
- Automated alerts
Instead of waiting for damage to occur, these systems detect unusual patterns and respond immediately.
How Secure IT Solutions Work Together
Secure IT solutions are not isolated tools. They function as a connected ecosystem.
For example:
- A suspicious login attempt triggers an alert.
- Multi-factor authentication blocks unauthorized access.
- Network monitoring detects abnormal traffic.
- Endpoint protection isolates affected devices.
- Backup systems ensure data recovery if needed.
Each component supports the others.
This layered model is often called “defense-in-depth.” If one layer fails, others remain active.
Secure IT Solutions vs Traditional IT Support
Many businesses confuse general IT support with secure IT solutions. While both are important, they serve different purposes.
| Traditional IT Support | Secure IT Solutions |
|---|---|
| Fixes technical issues | Prevents cyber threats |
| Focuses on hardware/software | Focuses on security strategy |
| Reactive approach | Proactive and continuous |
| Limited security coverage | Full infrastructure protection |
Businesses today need both operational IT support and secure IT solutions to remain competitive and protected.
Why a Multi-Layer Security Approach Is Essential
Cybercriminals do not rely on a single attack method. They combine:
- Phishing emails
- Malware downloads
- Credential theft
- Network exploitation
- Social engineering
Because threats are multi-dimensional, secure IT solutions must also be multi-layered.
Relying on a single security tool is like locking only your front door while leaving windows open.
Comprehensive secure IT infrastructure closes every possible entry point.
Why Secure IT Solutions Are Critical for Businesses Today
In 2026, cyber threats are no longer occasional problems—they are constant and sophisticated. Every business, from small startups to large enterprises, faces potential attacks. This makes secure IT solutions essential not just for protection, but for survival.
Secure IT solutions go beyond reactive problem-solving. They ensure proactive defense against threats, compliance with regulations, and continuous protection of sensitive business and customer data. Businesses without proper IT security are exposed to financial loss, reputational damage, and operational disruption.
The Rapid Growth of Cybersecurity Threats
Cyber threats have evolved in frequency, complexity, and creativity. Modern attackers use automation, artificial intelligence, and social engineering to exploit vulnerabilities. Common threats include:
- Ransomware attacks – Encrypt critical business data and demand payment for access.
- Phishing and social engineering – Trick employees into sharing credentials or sensitive data.
- Insider threats – Employees or contractors unintentionally or intentionally compromise data.
- Malware and spyware – Malicious software designed to steal, corrupt, or monitor data.
- Cloud misconfigurations – Improper cloud setups expose sensitive data publicly.
Secure IT solutions help prevent these attacks through layered security, real-time monitoring, and advanced detection methods.
Cyber Threat Trends Table
| Threat Type | Trend in 2026 | Impact on Businesses |
|---|---|---|
| Ransomware | Very High | Severe |
| Phishing | Extremely High | High |
| Insider Threats | Moderate | High |
| Cloud Attacks | Increasing | Severe |
| AI-Powered Attacks | Rapid Growth | Critical |
Implementing secure IT infrastructure reduces risk, prevents costly breaches, and ensures business continuity.
The Financial Impact of Ignoring Secure IT Solutions
Many businesses view cybersecurity as an optional expense, but the cost of a breach can far exceed the price of prevention.
Direct Costs of a Data Breach
- IT recovery expenses
- Legal fees
- Regulatory fines
- Customer compensation
Indirect Costs
- Operational downtime
- Lost productivity
- Damaged brand reputation
- Loss of customer trust
Example: Mid-Sized Business Breach
A mid-sized company suffered a ransomware attack due to outdated firewall systems. Consequences included:
- 5 days of operational downtime
- Loss of sensitive customer data
- Legal penalties and fines
- Extensive recovery costs exceeding $500,000
After the incident, the company implemented comprehensive secure IT solutions, including endpoint protection, cloud encryption, and 24/7 monitoring, which prevented future breaches.
Compliance and Regulatory Requirements
Secure IT solutions also help businesses comply with local and international regulations, which is increasingly mandatory.
Key compliance frameworks include:
- GDPR – Protects personal data of EU citizens
- HIPAA – Secures healthcare information in the US
- PCI-DSS – Ensures payment card data security
- ISO 27001 – Standard for information security management
- Industry-specific regulations for finance, healthcare, and government sectors
Failure to comply can result in fines, lawsuits, and reputational damage. Secure IT solutions include monitoring and reporting tools to maintain compliance efficiently.
Protecting Brand Reputation and Customer Trust
Customers expect their data to be secure. One breach can lead to permanent loss of trust.
Secure IT solutions ensure:
- Encryption of sensitive data
- Secure communication channels
- Multi-factor authentication
- Continuous monitoring for threats
Businesses that invest in IT security demonstrate responsibility and reliability, which enhances customer loyalty.
Enabling Business Growth Through Security
Security is not just protection—it is a growth enabler. Businesses with robust secure IT solutions can:
- Expand into cloud platforms safely
- Enable remote work with confidence
- Adopt AI and automation technologies
- Scale operations without exposing vulnerabilities
Without strong IT security, growth carries significant risks. With secure IT solutions, growth becomes safer and more sustainable.
Types of Secure IT Solutions for Businesses
Understanding the different types of secure IT solutions is essential for building a strong security strategy. Businesses face varied risks depending on size, industry, and technology use. The right combination of security tools and practices ensures comprehensive protection.
Secure IT solutions are multi-layered and designed to cover networks, devices, data, and user access points. Let’s explore the key types that modern businesses use.
Network Security Solutions
Network security is the backbone of any secure IT infrastructure. It protects the flow of data between devices, servers, and cloud systems. Without it, attackers can intercept or manipulate critical information.
Core components of network security include:
- Firewalls: Filter incoming and outgoing traffic to block malicious activity.
- Intrusion Detection Systems (IDS): Monitor for suspicious activity in real time.
- Intrusion Prevention Systems (IPS): Automatically block detected threats.
- Virtual Private Networks (VPNs): Ensure secure remote connections.
- Network segmentation: Isolates critical systems from general traffic to reduce risk.
Network security is the first layer of defense, keeping attackers out before they can access sensitive systems.
Endpoint Security Solutions
Every device connected to a network is an endpoint, which can become a target for cyberattacks. Endpoints include laptops, desktops, mobile devices, servers, and IoT devices.
Endpoint security tools include:
- Advanced antivirus and anti-malware software
- Endpoint Detection and Response (EDR) systems
- Automatic patch management
- Device encryption
Endpoint protection ensures that threats are contained before they spread across the organization. For example, a compromised laptop can be isolated quickly to prevent network-wide damage.
Cloud-Based Secure IT Solutions
Cloud computing is central to modern business operations. However, cloud environments are often targeted due to misconfigurations or weak access controls.
Secure IT solutions for cloud security include:
- Encryption of data at rest and in transit
- Multi-factor authentication (MFA)
- Secure access policies and role-based permissions
- Continuous monitoring of cloud activity
Proper cloud security reduces the risk of data exposure and ensures compliance with regulatory standards.
Data Protection and Backup Solutions
Data is a business’s most valuable asset. Secure IT solutions protect data through:
- End-to-end encryption
- Secure backup systems
- Disaster recovery planning
- Data Loss Prevention (DLP) tools
Backups are critical for business continuity. If ransomware or hardware failure occurs, businesses can quickly restore data without paying ransoms or losing operational capacity.
Identity and Access Management (IAM)
IAM systems control who can access which resources, ensuring only authorized users can interact with sensitive systems.
IAM features include:
- Role-based access control (RBAC)
- Multi-factor authentication (MFA)
- Biometric verification
- Single Sign-On (SSO)
- Monitoring of user activity
Many cyberattacks start with stolen credentials. IAM reduces this risk by adding verification layers and controlling access privileges.
Managed Secure IT Services
Managed services allow businesses to outsource security management to experts. These services provide:
- 24/7 monitoring and threat detection
- Security audits and compliance checks
- Incident response and remediation
- Software updates and patch management
Benefits of managed services:
- Access to cybersecurity expertise
- Reduced internal workload
- Predictable monthly costs
- Faster threat detection and response
Managed secure IT solutions are ideal for businesses without in-house IT security teams.
Summary of Secure IT Solution Types
| Secure IT Solution Type | Purpose |
|---|---|
| Network Security | Protects data flow and network integrity |
| Endpoint Security | Secures individual devices from threats |
| Cloud Security | Protects cloud platforms and stored data |
| Data Protection & Backup | Ensures recovery and prevents data loss |
| Identity & Access Management | Controls user access and reduces insider threats |
| Managed Security Services | Provides continuous expert monitoring and support |
Each type works together to create a comprehensive, multi-layered secure IT infrastructure.
What Are the Benefits of Secure IT Solutions
Implementing secure IT solutions is not just about protection—it’s about enhancing business resilience, efficiency, and trust. Modern businesses face constant cyber threats, regulatory demands, and operational challenges. Investing in a comprehensive IT security framework delivers measurable benefits across every aspect of an organization.
Protection Against Cyber Attacks
The most obvious benefit is defense against cybercrime. Secure IT solutions protect businesses from:
- Ransomware attacks – Prevents critical systems and data from being locked or held hostage.
- Phishing and social engineering – Reduces the risk of employees inadvertently giving away sensitive information.
- Malware, spyware, and viruses – Stops malicious software from infecting devices and spreading across networks.
- Unauthorized access – Blocks hackers from infiltrating networks, cloud environments, and databases.
Companies with layered secure IT solutions experience significantly fewer successful attacks and can respond more quickly if a threat occurs.
Business Continuity and Disaster Recovery
Secure IT solutions ensure that operations can continue even in the event of a cyberattack, natural disaster, or technical failure. Key features include:
- Regular automated backups of critical data
- Disaster recovery plans for restoring IT infrastructure
- Redundant systems to minimize downtime
- Business continuity procedures that allow employees to work remotely without interruption
Businesses without secure IT solutions risk prolonged downtime, which can cost thousands or even millions of dollars depending on the industry.
Increased Customer Trust and Brand Reputation
Customers expect their personal information to be protected. Secure IT solutions help businesses:
- Safeguard customer data through encryption and access control
- Demonstrate compliance with industry regulations
- Build credibility and reliability in the market
According to surveys, over 80% of consumers are less likely to engage with a company after a data breach. Strong IT security is therefore an investment in reputation, not just protection.
Improved Productivity
Cyber incidents can halt business operations and decrease employee efficiency. Secure IT solutions:
- Reduce downtime caused by malware or technical failures
- Streamline security processes so employees can work safely
- Provide remote work solutions with secure access
- Automate monitoring and threat detection to minimize manual intervention
By preventing disruptions, businesses can maintain productivity and focus on growth.
Scalability and Flexibility
As businesses grow, IT systems must adapt. Secure IT solutions provide:
- Scalable security for expanding networks and devices
- Cloud-first security that supports remote teams and SaaS tools
- Advanced tools to integrate with new applications and technologies
Investing in secure IT infrastructure allows businesses to grow without compromising security.
Regulatory Compliance and Legal Protection
Many industries require businesses to maintain strict security standards. Secure IT solutions:
- Ensure adherence to GDPR, HIPAA, PCI-DSS, and ISO 27001
- Maintain audit trails for compliance reporting
- Reduce risk of fines, lawsuits, and operational restrictions
Compliance is no longer optional. Secure IT solutions provide the tools to meet these requirements efficiently.
Summary of Benefits
| Benefit | Explanation |
|---|---|
| Cyber Attack Protection | Blocks malware, ransomware, phishing, and unauthorized access |
| Business Continuity | Minimizes downtime and ensures quick recovery |
| Customer Trust | Protects data and strengthens brand reputation |
| Productivity | Reduces operational disruptions and maintains efficiency |
| Scalability | Supports business growth and technology integration |
| Compliance | Meets industry regulations and reduces legal risk |
Secure IT solutions are an investment in long-term business resilience, growth, and trust.
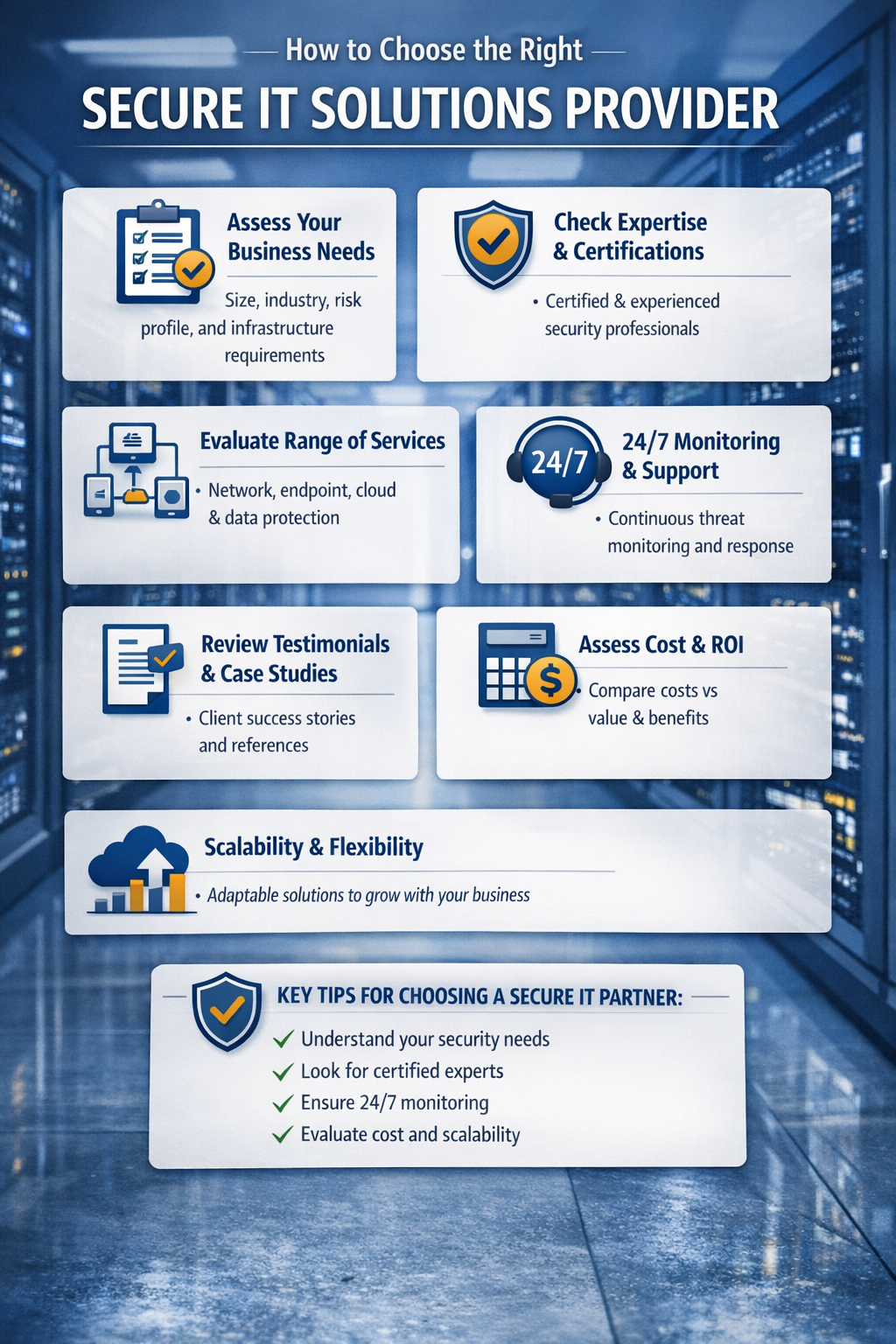
How to Choose the Right Secure IT Solutions Provider
Selecting the right provider for secure IT solutions is critical. The right partner not only implements security tools but also provides ongoing support, monitoring, and strategic guidance. A poor choice can leave your business vulnerable or overspend on unnecessary solutions.
Here’s a step-by-step guide to choosing the right provider.
Assess Your Business Needs
Before searching for a provider, understand your business’s specific requirements:
- Size of the organization – Larger businesses require more complex, layered solutions.
- Industry regulations – Healthcare, finance, and e-commerce have strict compliance needs.
- Technology infrastructure – Cloud-based, on-premises, or hybrid systems require different approaches.
- Risk profile – Identify your most valuable data and assets and prioritize their protection.
By understanding these factors, you can narrow your search to providers that specialize in your business type and risk level.
Check Provider Expertise and Certifications
Security expertise matters. Look for providers with:
- Certified security professionals (CISSP, CISM, CEH)
- ISO 27001 certification or similar compliance credentials
- Experience in your industry
- Proven track record of implementing secure IT solutions for businesses of similar size
A knowledgeable provider can tailor solutions to your unique business environment.
Evaluate the Range of Services
A good secure IT solutions provider offers comprehensive coverage, including:
- Network security
- Endpoint protection
- Cloud security and monitoring
- Data backup and disaster recovery
- Identity and access management
- Managed security services
- Compliance support
Avoid providers that specialize in only one area unless your needs are very specific. Comprehensive solutions provide layered protection and reduce gaps.
Consider 24/7 Monitoring and Support
Cyber threats can occur at any time. Ensure your provider offers:
- 24/7 threat monitoring
- Rapid incident response
- Security updates and patch management
- Continuous vulnerability assessments
Immediate detection and response can prevent minor issues from becoming major breaches.
Review Client Testimonials and Case Studies
Research past clients and success stories:
- Ask for references or case studies in your industry
- Look for metrics like breach prevention, downtime reduction, and compliance achievement
- Evaluate customer service and responsiveness
Real-world examples demonstrate the provider’s ability to deliver results.
Assess Cost and ROI
Cost is important, but value matters more. Consider:
- Upfront costs vs ongoing subscription or managed services fees
- The scope of coverage included in the package
- Potential savings by avoiding breaches, downtime, and fines
A quality provider offers predictable pricing with measurable security benefits, making it a long-term investment rather than a short-term expense.
Look for Scalability and Flexibility
Your business will grow, and your IT needs will evolve. A good provider offers:
- Scalable solutions to accommodate growth
- Flexibility to integrate new technologies
- Options for cloud, hybrid, or on-premises environments
Scalable secure IT solutions prevent the need to completely overhaul your security as your business expands.
A strategic partnership with the right secure IT solutions provider ensures long-term protection, compliance, and peace of mind.